The malware can run scripts and performs its tasks without interference and that can be devastating. Linux is becoming an increasingly attractive target among cyber criminals due to its growing popularity and the high-value devices it powers worldwide. Effective security is contingent upon defense in depth, and kernel security is a key element of overall system security that cannot be overlooked. After all, the kernel is the foundation of a system, and if the kernel is not secure, then nothing on the system is secure. It is unfortunately quite common for administrators to disable SELinux or AppArmor when they encounter an issue as opposed to learning how to fix the issue with these services enabled.
- All in all, you can run it to protect your PC well.
- Every user accesses the published application, the user automatically becomes the local administrator group on the VDA server so that the user can remote desktop the VDA server.
- However, that doesn’t mean that you’ll need to ditch your antivirus when the system behavior takes the wrong turn.
Using Disk Drill, you can scan your drive for recoverable data and restore it to a folder of your choice. To fix this, you can simply restore access to the built-in administrator account that you were likely using. When you regain access, you can move your data across to the newly created Microsoft user account.
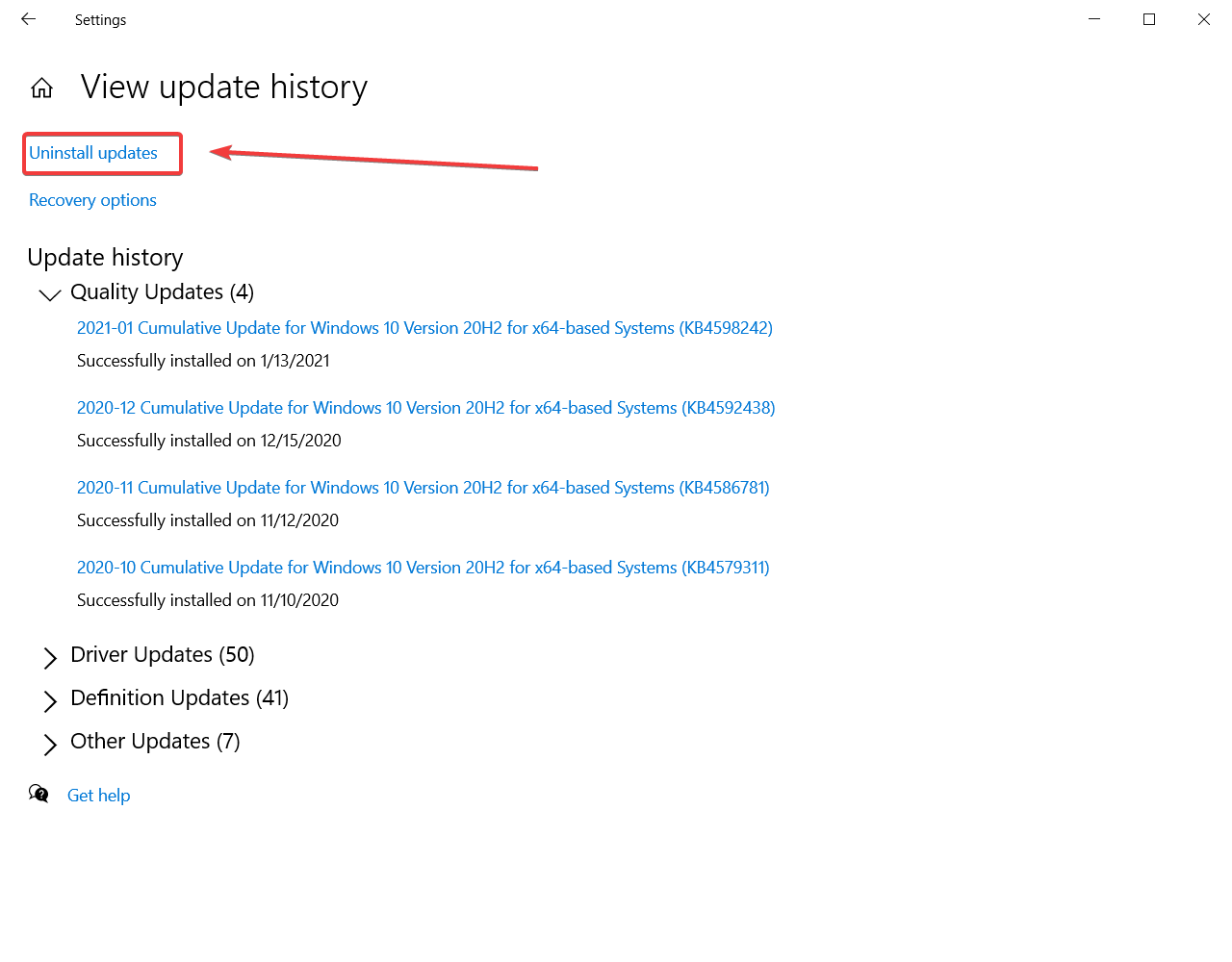
A Look At Trouble-Free Missing Dll Files Methods
The same .ini files are used for both the ‘console’ version of the launcher (i.e. py.exe) and for the ‘windows’ version (i.e. pyw.exe) rocketdrivers.com/dll/comctl32_dll. In this dialog, you can add or modify User and System variables. To change System variables, you need non-restricted access to your machine (i.e. Administrator rights). These changes will apply to any further commands executed in that console, and will be inherited by any applications started from the console. As with the application use, packages can be installed to any location as there is an opportunity to specify search paths before initializing the interpreter. Otherwise, there is no fundamental differences between using the embedded distribution and a regular installation.
- One of the tasks the operating system performs is to update the CR3 value in the CPU during context switches.
- In the file explorer, right-click on the address bar and select “Delete History” option.
- The folders within OneDrive will sync automatically with the OneDrive folders in File Explorer in Windows 10.
The CRC is one of the most commonly used techniques for error detection in data communications. Parity is used in RAID-3, RAID-4, and RAID-5 to validate the data written to the RAID array. Parity across the array is computed using the XOR logical operation. The parity information in RAID can either be stored on a separate, dedicated drive, or be mixed with the data across all the drives in the array.
Understanding Quick Advice Of Dll Files
For example, you can decide which system and apps icons to be shown in system tray on Windows 10. Firefox automatically checks your spelling as you type. Available options include adding dictionaries and removing words added by accident. Firefox stores your personal information and settings in a profile folder.
Leave a Reply